CVE-2015-7349 - Reflected cross-site scripting vulnerability in DIGIPASS authentication for Citrix Web Interface
1. Vulnerability Properties
Title: Reflected cross-site scripting vulnerability in DIGIPASS authentication for Citrix Web Interface
CVE ID: CVE-2015-7349
CVSSv3 Base Score: 4.3 (AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:N/A:N)
Vendor: Vasco (https://www.vasco.com)
Products: DIGIPASS authentication for Citrix Web Interface
Advisory Release Date: 6 October 2015
Advisory URL: https://labs.integrity.pt/advisories/cve-2015-7349
Credits: Discovery by Filipe Bernardo <fb[at]integrity.pt>
2. Vulnerability Summary
Vasco DIGIPASS authentication for Citrix Web Interface is vulnerable to Cross-site scripting (XSS) on the login page.
The DIGIPASS plug-in is installed on IIS server and when a user attempts to login and an error occurs, this plugin handles the action and shows an error message displaying the reason. The failmessage parameter is vulnerable to XSS.
3. Technical Details
When a login error occurs the failmessage parameter displays an error message from the DIGIPASS plug-in with the information regarding the error.
This failmessage parameter is vulnerable and it's possible to inject javascript code that is reflected and runs on the client browser. To exploit this an attacker only needs to provide a link to a user with a manipulated failmessage payload to execute code in the victim browser.
The standard URL of the vulnerable Authentication page is the following:
- www.yourdomain.com/Citrix/XenApp/auth/login.aspx
The vulnerable parameter is failmessage.
The attacker only needs to prepare an link with a javascript payload and the share this with a user, upon clicking the link the javascript will run on the client browser, the following image shows an example payload running the javascript and accessing the browser cookies:
[caption id="attachment_470" align="alignnone" width="938"]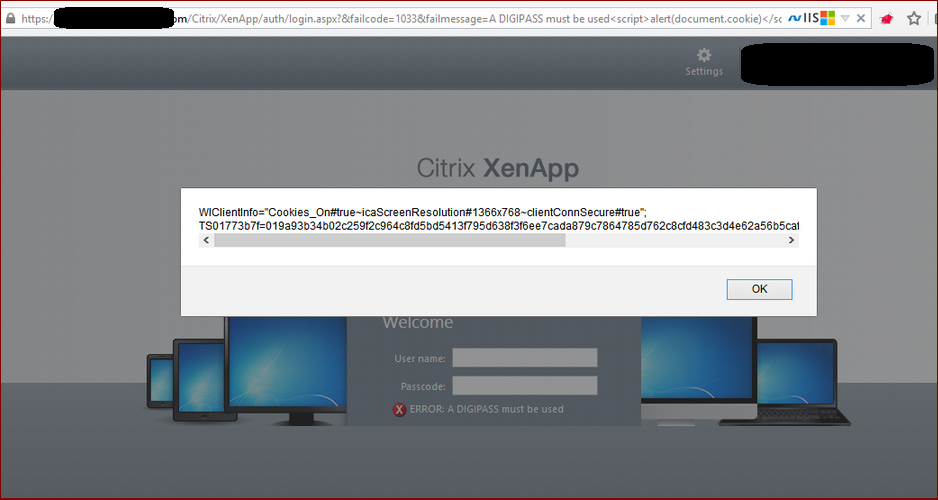 Vasco DIGIPASS XSS[/caption]
Vasco DIGIPASS XSS[/caption]
4. Vulnerable Versions
- Assume all the VASCO DIGIPASS for Citrix Web Interface existent to the date.
5. Solution
- To mitigate this clients should "disable the display of the login failure reason" as mentioned in the VASCO KB140148
6. References
- https://www.vasco.com/support/psirt/security-advisories/reflected-cross-site-scripting-vulnerability-in-digipass-authentication-for-citrix-web-interface/default.aspx
- https://www.vasco.com/Images/Security-Advisory-DPAuth4CWI-v0.2.pdf
- https://www.vasco.com/images/kb_140148.pdf
7. Vulnerability Timeline
- 25/03/2015 - Reported to Citrix Security team
- 03/07/2015 - Citrix analysed and reported that the problem is related to the Vasco Plug-in
- 11/08/2015 - Reported to Vasco security team (PSIRT)
- 19/08/2015 - Vasco PSIRT acknowledged vulnerability
- 25/09/2015 - Vasco PSIRT released the fix and advisory
- 06/10/2015 - Advisory published
Latest Advisories
- CVE-2025-55107 - Stored Cross-Site Scripting in ArcGIS Enterprise Sites
- CVE-2025-55103 - Stored Cross-Site Scripting in ArcGIS Enterprise Sites
- CVE-2025-53122 - SQLi in OpenNMS Horizon and Meridian
- CVE-2025-53121 - Multiple stored XSS in OpenNMS Horizon
- CVE-2025-48953 - Umbraco Vulnerable to By-Pass of Configured Allowed Extensions for File Uploads
Latest Articles
- The Curious Case of Apple iOS IKEv2 VPN On Demand
- Gmail Android app insecure Network Security Configuration.
- Reviewing Android Webviews fileAccess attack vectors.
- Droidstat-X, Android Applications Security Analyser Xmind Generator
- Uber Hacking: How we found out who you are, where you are and where you went!
© 2026 INTEGRITY S.A. All rights reserved. | Cookie Policy