Insecure Direct Object Reference in OSTicket attachments
1. Vulnerability Properties
Title: Insecure Direct Object Reference in OSTicket attachments
CVE ID: Pending
CVSSv3 Base Score: 6.5 (AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N)
Vendor: osTicket
Products: osTicket 1.8
Advisory Release Date: 24 February 2016
Advisory URL: https://labs.integrity.pt/advisories/osticket-possibility-to-download-files-from-other-users
Credits: Discovery by Fábio Pires <fp[at]integrity.pt>
2. Vulnerability Summary
A remote attacker is able to download a document attached to a ticket by any other user.
3. Technical Details
What is osTicket, you ask:
osTicket is a widely-used and trusted open source support ticket system. It seamlessly routes inquiries created via email, web-forms and phone calls into a simple, easy-to-use, multi-user, web-based customer support platform. osTicket comes packed with more features and tools than most of the expensive (and complex) support ticket systems on the market. The best part is, it’s completely free.
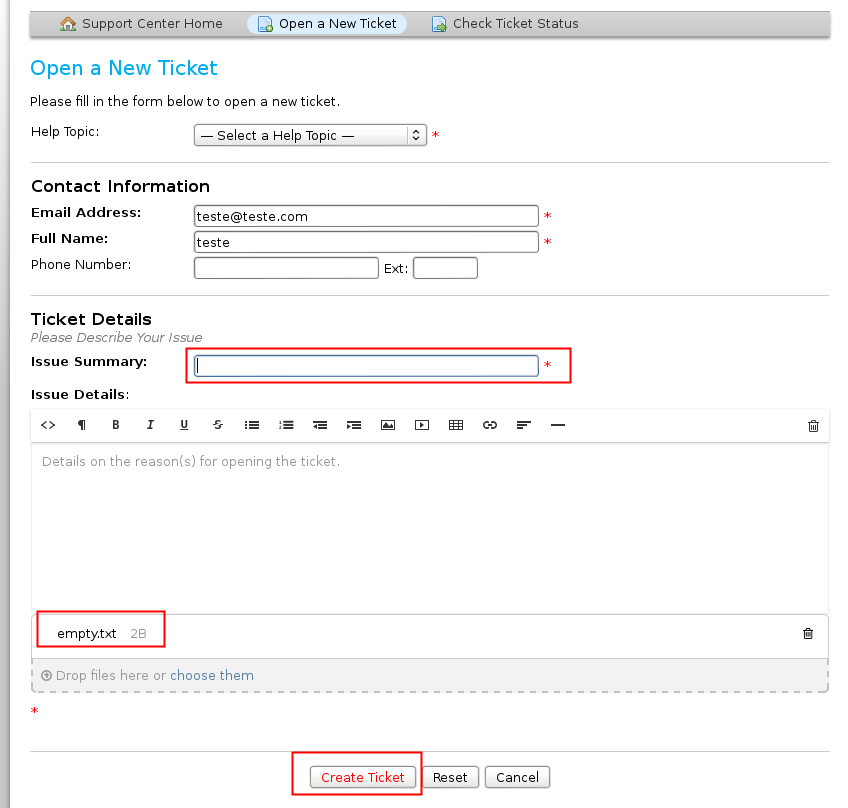
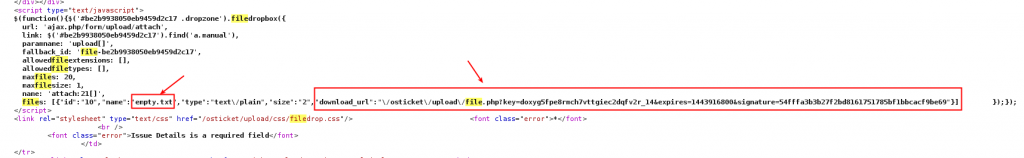
First of all you need to create a new ticket, select a file to attach and leave at least one field empty
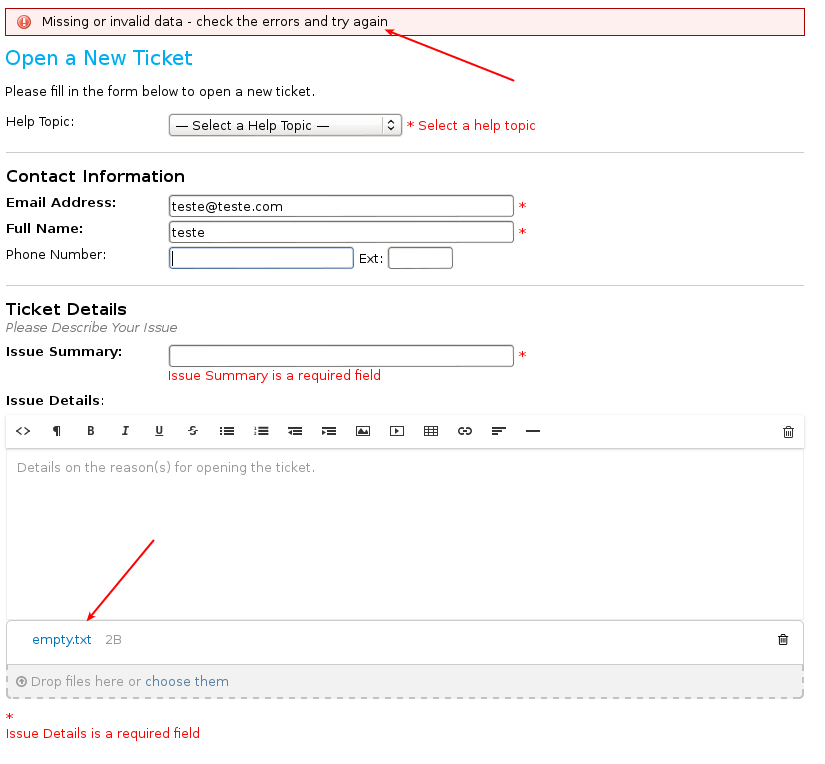
After your submission, you get an error about “missing data”.
You can notice that the attached file is now a link and you can download it:
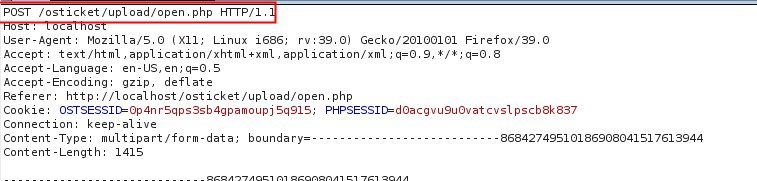
Meanwhile, an ajax request (POST) was sent to the server.
This request uploads the file to the server and server replied with an ID.
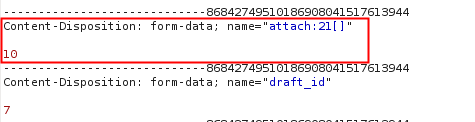
Another request is sent to the server in order to associate the previous ID to the ticket that you’re submiting. (next image, id 10)
As you can see in the previous request, the ID: 10 was sent as an attachment to your ticket.
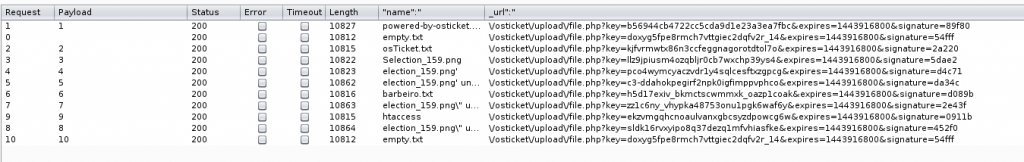
When you submit this request, the server will reply with the file name associated to ID:10 and the download_url.
Automating this process, by sending the attach id starting from 1 to 10 (last generated id), you get all the files uploaded to the server, with the respective download url.
3. Solution
Latest version available for download through the OSTicket website is still vulnerable at the time of this advisory. Development version on github is fixed.
4. Vulnerability timeline:
- September 30, 2015 — “Where to report” mail sent to osTicket
- October 02, 2015 — osTicket’s SupportSystem Team reply with: “Thanks for your email. You can report any findings on our GitHub project page. Thanks! ”
- October 02, 2015 — Bug reported to osTicket’s github project page.
- October 03, 2015 — Bug fixed.
- October 04, 2015 — Fix merged to dev release.
- February 24, 2016 — Public disclosure.
5. References:
- https://github.com/osTicket/osTicket-1.8/issues/2615
- https://github.com/osTicket/osTicket-1.8/pull/2618
Latest Advisories
- CVE-2025-55107 - Stored Cross-Site Scripting in ArcGIS Enterprise Sites
- CVE-2025-55103 - Stored Cross-Site Scripting in ArcGIS Enterprise Sites
- CVE-2025-53122 - SQLi in OpenNMS Horizon and Meridian
- CVE-2025-53121 - Multiple stored XSS in OpenNMS Horizon
- CVE-2025-48953 - Umbraco Vulnerable to By-Pass of Configured Allowed Extensions for File Uploads
Latest Articles
- The Curious Case of Apple iOS IKEv2 VPN On Demand
- Gmail Android app insecure Network Security Configuration.
- Reviewing Android Webviews fileAccess attack vectors.
- Droidstat-X, Android Applications Security Analyser Xmind Generator
- Uber Hacking: How we found out who you are, where you are and where you went!
© 2026 INTEGRITY S.A. All rights reserved. | Cookie Policy